Phishing emails are designed by fraudsters to appear as if they have been sent by banks, credit card companies, government departments, online stores auction sites, and other trusted organisations. You can receive phishing emails via a dedicated email client (program) either such as Microsoft Outlook, or via internet-based email such as Gmail, Hotmail, Yahoo! Mail or that supplied by your ISP.
Phishing emails attempt to trick you into either:
- Clicking on a link to visit a hoax but authentic-looking website which either requests confidential information or is infected with malware.
- Opening an attachment disguised as a legitimate file such as a document or .exe file, but which actually contains malware.
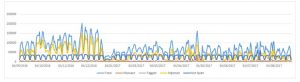
We wanted to assure staff that Information Services take steps on a daily basis to remove spam and Phishing emails from staff email. The graph below shows a one-week period from the last year. This highlights the amount of spam taken out of the staff email system by our filters.
In this week, the mail server rejected 150,000 emails as they were above the threshold to even be passed to staff email accounts (see the yellow line in the chart above)
The blue line in the chart above is the total amount of email received by the mail server. A huge proportion of mail received is spam and is never delivered. The amount of mail received that is tagged is spam is not much when you look at the overall amount of email received in the first instance.
When mail arrives at the mail server it rates messages giving them a score.
0-5 are not tagged as spam and are delivered
5-15 are tagged as spam and will be directed to your spam folder
15> these are not delivered.
Unfortunately, the mail server is unable to detect all email that may be spam and you will get a small amount of mail into your inbox, which has not been tagged as spam. You need to be able to identify which emails are genuine and which emails you should be suspicious off.
- The sender’s email address may be different from the trusted organisation’s website address.
- The email may sent from a completely different address or a free webmail address.
- The email may not use your proper name, but uses a non-specific greeting such as “Dear customer.”
- It may contain misspelt words and poor grammar.
- A sense of urgency; for example the threat that unless you act immediately your account may be closed.
- A prominent website link. These can be forged or seem very similar to the proper address, but even a single character’s difference means a different website.
- A request for personal information such as username, password or bank details.
- You weren’t expecting to get an email from the organisation that appears to have sent it.
- The entire text of the email is contained within an image rather than the usual text format. The image contains an embedded link to a bogus site.
- Some phishing emails actually warn you of a virus and invite you to click on a link or open an attachment to protect yourself.
- Even an email from a trusted source may actually be a phishing email if the sender’s account has been hacked.
Extracts from GetSafeOnline (https://www.getsafeonline.org/online-safety-and-security/email/ )
Information Services will continue to increase cyber resilience at University of Stirling and will be collaborating with The NCSC (National Cyber Security Centre) to try to reduce the amount of scam operators.
If you think you have received an email that may be fraudulent, you should send the entire message as an attachment to us on InfoSecurityTeam@stir.ac.uk . We will forward it to a service set up for public sector organisations who work to have the sites responsible taken down by their ISPs. They have more power than any individual person or organisation so this is a useful service. You may continue to receive these type of emails, as Information Services are not actually able to block them. It may take some time for the National Cyber Security Centre in collaboration with Netcraft to initiate takedown notices to the hosts of the mail and Phishing sites.
Our hope is that the level of reporting will reach the point where takedowns start to impact on the profitability of this type of scam. Even before that, the action will reduce the number of targets reached by the scam operators, which has to be good for everyone.