Over the last few days, we have seen a number of reported incidences of what is known as ‘Whaling’ or ‘Whale phishing’.
Whaling is a type of fraud or phishing scheme that targets high-profile end-users, usually senior staff in an organisation, politicians, and celebrities. Fraudsters behind whaling campaigns aim to trick targets into giving out their personal information and/or business credentials.
The examples we’ve seen recently come from a made up email address e.g. gerry.mccormack@my.com and are sent to people who work with the person concerned. They often start with an innocuous question like ‘Are you on campus?’. If a reply is made, they then go on to spin a story about them having an urgent need for money to be transferred, something to be purchased and sent to them or something similar. In the examples we’ve seen, they ask the staff member to buy iTunes vouchers, scratch the foil off to reveal the voucher number, take a photo and send it to them.
So how do you identify these emails when they hit your inbox? You must be aware of the ‘From’ field in emails – an external email like the fake one above, will appear in Outlook as ‘Gerry McCormack <gerry.mccormack@my.com>’. This is clearly not a University address and you should never assume that your boss, manager etc is emailing from their personal email account. Why would they? If in doubt, contact them separately to confirm the email is legitimate.
If you receive an email of this sort – DELETE IT. Do not reply to it. There’s no need to report to the Information Centre unless you are worried.
If you are not sure whether an email is legitimate or not, please contact the Information Centre and we will help you.
SPEAR PHISHING EMAIL CIRCULATING TARGETING SENIOR STAFF
The Scottish Government has also made us aware of a sophisticated phishing email which is being sent to those with financial authority in an organisation. The email is well written but does not address the receiver by name. It has a Word attachment with a name that looks like an invoice number. The Word file contains a link to login to download the content of the document via Office 365 (see image below). If clicked, a Trojan is downloaded to the receiver’s PC.
If you receive a suspicious document, don’t open it. If you were not expecting an invoice, don’t open it. If it seems suspicious, trust your gut.
If you are not sure whether an email is legitimate or not, please contact the Information Centre and we will help you.
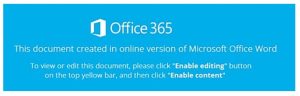
Image in header is courtesy of: https://digitalguardian.com/blog/dont-get-hooked-how-recognize-and-avoid-phishing-attacks-infographic
#stircybersec